DKIM Verification
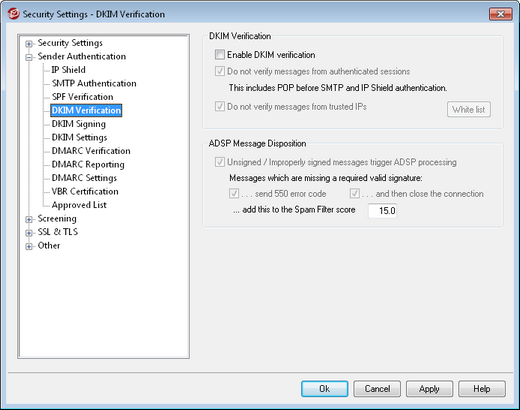
Use this screen to configure MDaemon to verify DomainKeys Identified Mail (DKIM) signatures in incoming remote messages. When this feature is enabled and an incoming message has been cryptographically signed, MDaemon will retrieve the public key from the DNS record of the domain taken from the signature and then use that key to test the message’s DKIM signature to determine its validity.
If the signature passes the verification test, the message will continue on to the next step in the regular delivery process. Additionally, if the domain taken from the signature also appears on the Approved List, the message’s Spam Filter score will receive a beneficial adjustment.
If a message has no signature, or if the signature is invalid, MDaemon will query DNS for the Author Domain Signing Practices (ADSP) record of the domain in the From header to determine whether or not all of that domain’s messages should be signed. If the ADSP record indicates that a valid signature is required and the public key indicates that the signer is not merely testing DKIM, the message will receive a "Fail" result and be treated accordingly—it can be rejected outright or accepted but have its Spam Filter score adjusted upward.
Finally, if a site's ADSP record uses a syntax unknown to MDaemon, if no record exists at all, or if the ADSP Message Disposition option below is disabled, then no punitive measures will be taken. The unsigned or invalidly signed message will be treated as if the domain signs only some of its messages.
For more on DKIM see: http://www.dkim.org/
DKIM Verification
Enable DKIM verification
Click this option to enable DomainKeys Identified Mail verification of incoming remote messages. This option is required if you have SecurityPlus for MDaemon installed and wish to use its Urgent Updates feature.
Do not verify messages from authenticated sessions
Click this option if you want to exempt messages from cryptographic verification when the message session is authenticated. Authenticated sessions include those verified via SMTP Authentication, POP before SMTP, or the IP Shield.
Do not verify messages from trusted IPs
Use this option if you want connections from trusted IP addresses to be exempt from DKIM verification.
White list
Click this button to open the exception list. Messages originating from any IP addresses specified on the list will not be subject to cryptographic verification.
ADSP Message Disposition
Unsigned/Improperly signed messages trigger ADSP processing
Enable this option if you wish to query for and honor Author Domain Signing Practices (ADSP) records when an incoming message is unsigned or improperly signed. If this option is disabled or if the ADSP record uses a syntax unknown to MDaemon, then the message will be treated as if the domain signs only some of its messages.
Messages which are missing a required valid signature:
...send 550 error code
When the ADSP record indicates that a valid signature is required, any message without one will be rejected—MDaemon will return the 550 code and reject the message during the SMTP process. If, however, the signer’s public key indicates that the signer is merely testing DKIM, the message will be processed normally.
...and then close the connection
Click this option if you wish to close the connection to the sending server when a message is rejected according to the previous option. If this option is disabled then the message will still be rejected according to the previous option but the connection will be allowed to continue.
...add this to the Spam Filter score
When the ADSP record indicates that a valid signature is required, any message without one will have this value added to its Spam Filter score. If, however, you have enabled the "...send 550 error code" option above, the message will be rejected as invalid without having to be processed through the Spam Filter. In all cases, if the signer’s public key indicates that the domain is “testing,” no action will be taken—the Spam Filter score will not be modified.
|
Using this option could still cause a message to be rejected if the resulting Spam Filter score exceeds the SMTP rejection threshold designated on the Spam Filter screen. |
Authentication-Results header
Whenever a message is authenticated using SMTP AUTH, SPF, DomainKeys Identified Mail, or DMARC, MDaemon will insert the Authentication-Results header into the message, listing the results of the authentication process. If MDaemon is configured to accept messages even when they fail authentication, then the Authentication-Results header will contain a code to identify the reason for the failure.
|
There is ongoing work via the Internet Engineering Task Force (IETF) on this header and the authentication protocols mentioned in this section. You can find more information on this at the IETF web site, located at: http://www.ietf.org/. |
DKIM Headers in Mailing List Messages
By default, MDaemon strips DKIM signatures from incoming list messages because those signatures can be broken by changes made to the message headers or content during list processing. If you would like MDaemon to leave signatures in list messages, you can configure it to do so by manually setting the following option in the MDaemon.ini file:
[DomainKeys]
StripSigsFromListMail=No (default is "Yes")
See:

