Hijack Detection
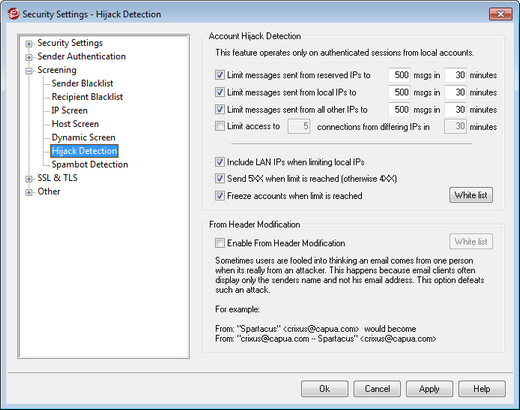
Account Hijack Detection
The options on this screen can be used to detect a possibly hijacked MDaemon account and automatically prevent it from sending messages through your server. For example, if a spammer somehow obtained an account's email address and password then this feature could prevent the spammer from using the account to send bulk junk e-mail through your system. You can designate a maximum number of messages that may be sent by an account in a given number of minutes, based on the IP address from which it is connecting. You can also choose to disable accounts that reach the limit. There is also a White List that can be used to exempt certain addresses from this restriction. Account Hijack Detection is enabled by default.
|
Account Hijack Detection only applies to local accounts over authenticated sessions, and the Postmaster account is automatically exempt. |
Limit messages sent from reserved IPs to [xx] msgs in [xx] minutes
Use this option to prevent MDaemon accounts connecting from reserved IPs from sending more than the specified number of messages in the designated number of minutes. Reserved IP addresses are mostly as defined by RFCs (for example, 127.0.0.*, 192.168.*.*, 10.*.*.*, 172.16.0.0/12, ::1, FD00::/8, FEC0::/10, and FE80::/64).
Limit messages sent from local IPs to [xx] msgs in [xx] minutes
Use this option to prevent MDaemon accounts connecting from any local IPs from sending more than the specified number of messages in the designated number of minutes. Local IPs are all IP addresses configured for any of your MDaemon domain.
Limit messages sent from all other IPs to [xx] msgs in [xx] minutes
Use this option to prevent MDaemon accounts connecting from any other IPs from sending more than the specified number of messages in the designated number of minutes.
Limit access to [xx] connections from differing IPs in [xx] minutes
Use this option to limit the number of connections from different IP addresses allowed within the specified number of minutes. For example, in normal circumstances if your account is accessed from ten different IP addresses within just a few minutes, it is likely the account has been hijacked. This option is disabled by default.
Include LAN IPs when limiting local IPs
By default LAN IPs are included when using the "Limit messages sent from local IPs..." option above. Uncheck this box if you do not wish to include LAN IPs when limiting local IPs.
Send 5XX when limit is reached (otherwise 4XX)
By default when one of the limits is reached, MDaemon will send a 5XX reply code to the hijacked account. Disable this option if you wish to send a 4XX code instead.
Freeze accounts when limit is reached
Check this box if you wish to freeze accounts that attempt to send more than the allowable number of messages. When this happens, the server sends a 552 error, the connection is dropped, and the account is immediately frozen. The frozen account will no longer be able send mail or check its mail, but MDaemon will still accept incoming mail for the account. Finally, when the account is frozen an email is then sent to the postmaster about the account. If the postmaster wishes to re-enable the account, he can simply reply to the message.
White List
Use the White List to designate any addresses that you wish to exempt from Account Hijack Detection. Wildcards are permitted. For example, "newsletters@example.com" would exempt example.com's "newsletters" MDaemon account, while "*@newsletters.example.com" would exempt all MDaemon accounts belonging to the newsletters.example.com domain. The Postmaster account is automatically exempt from Account Hijack Detection.
From Header Modification
This security feature modifies the "From:" header of incoming messages to cause the name-only portion of the header to contain both the name and email address. This is done to combat a common tactic used in spam and attacks where the message is made to appear to be coming from someone else. When displaying a list of messages, email clients commonly display only the sender's name rather than the name and email address. To see the email address, the recipient must first open the message or take some other action, such as right-click the entry, hover over the name, or the like. For this reason attackers commonly construct an email so that a legitimate person or company name appears in the visible portion of the "From:" header while an illegitimate email address is hidden. For example, a message's actual "From:" header might be, "Honest Bank and Trust" <lightfingers.klepto@example.com>, but your client might display only "Honest Bank and Trust" as the sender. This feature changes the visible portion of the header to display both parts, with the email address given first. In the above example the sender would now appear as "lightfingers.klepto@example.com -- Honest Bank and Trust," giving you a clear indication that the message is fraudulent.
Enable From header modification
Enable this option if you wish to modify the client-visible portion of the "From:" header of incoming messages to include both the name and email address of the sender. The construction of the new header will change from "Sender's Name" <mailbox@example.com> to "mailbox@example.com -- Sender's Name" <mailbox@example.com>. This only applies to messages to local users, and this option is disabled by default. Consider carefully before enabling this option as some users may neither expect nor want the From: header to be modified, even if it might help them identify fraudulent emails.

