DKIM Signing
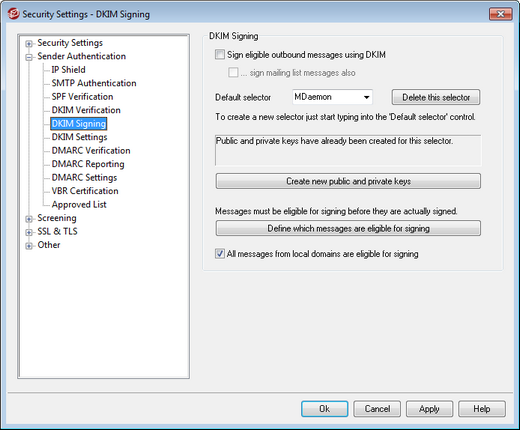
Use the options contained on the DKIM Signing screen to configure MDaemon to sign eligible outbound messages using DKIM, and to define the criteria that will make a message eligible. You can also use this screen to designate selectors and generate corresponding public and private keys suitable for use with the DKIM specification. A default selector ("MDaemon") and a default public and private key are created for you automatically on startup. All keys are unique—they are never the same from one site to another, regardless of the selector specified. By default, keys are generated with a secure bit depth of 1024 bits.
DKIM Signing
Sign eligible outbound messages using DKIM
Click this option if you wish to use DomainKeys Identified Mail to cryptographically sign some outgoing messages. In order for a message to be signed, it must meet the criteria designated under the Define which messages are eligible for signing button and be received by MDaemon for delivery on an authenticated session. There is also a Content Filter action, "Sign with DKIM selector..." that you can use to cause messages to be signed.
...sign mailing list messages
Click this check box if you wish to cryptographically sign all outgoing Mailing List messages. Because MDaemon will sign all mail to all of your lists, you do not need to use the "Define which messages are eligible for signing" option to authorize them for cryptographic signing.
|
Signing list mail requires content filter processing for each list message after "cracking" the list. This could affect server performance when dealing with large and highly active mailing lists. |
Default selector
From the drop-down list, choose the selector whose corresponding public/private key pair you wish to use when signing messages. If you wish to create a new key pair with a different selector, type the desired selector name here and click "Create new public and private keys" below. If you wish to sign some messages using an alternate selector, designate a specific selector under the "Define which messages are eligible for signing" option, or create a Content Filter rule using the "Sign with DKIM selector..." action.
Delete this selector
Click this button if you wish to delete a selector. Follow the on-screen instructions that appear.
Create new public and private keys
Click this button to generate a public/private key pair for the selector specified above. A public/private key pair will be generated for the selector, and the file dns_readme.txt will be generated and automatically opened. This file contains example DKIM data that you will need to publish to your domain's DNS records listing your DKIM Policy and the public key for the designated selector. The file lists samples for both testing and not testing status, and for whether you are signing all messages or just some messages originating from your domain. If you are currently testing DKIM or this selector, then you will need to use the information contained in the Testing entries for either the Policy or the selector, depending on what you are testing. Otherwise you will need to use the Not Testing entries.
All keys are stored in PEM format, and all selectors and keys are stored under the \MDaemon\Pem folder in the following way:
\MDaemon\Pem\<Selector>\rsa.public - public key for this selector
\MDaemon\Pem\<Selector>\rsa.private - private key for this selector
|
The files contained in these folders are not encrypted or hidden, but they contain RSA private encryption keys that should never be accessed by anyone without permission. You should therefore take steps to secure these folders and subfolders using your OS tools. |
Define which messages are eligible for signing
If you have elected to sign eligible outbound messages, click this button to edit the DKSign.dat file, which contains the list of domains and addresses that MDaemon will use to determine whether or not a message should be signed. For each address listed you must designate whether or not the message should be To or From that address in order for it to qualify to be signed, or you can designate some other header such as "Reply-To" or "Sender". Optionally, you can designate a selector for each entry, which will be used when signing a message that matches that entry. Finally, you can specify an optional signing domain to be used in the "d=" tag within the signature header. This can be useful, for example, when you have multiple sub-domains signing messages. In such cases you could use the "d=" tag to tell the receiving servers to look for the DKIM keys in a single domain's DNS record, thus making it possible for you to manage all of the keys in one record rather than having to manage separate records for each sub-domain. Wildcards are permitted in domains and addresses.
All messages from local domains are eligible for signing
Use this option if you wish to make all messages from your local domains eligible for signing. If you use this option then you do not need to add any of your local domains to the eligibility list (i.e. the DKSign.dat file) unless you wish to designate a specific selector or "d=" tag to be used when signing a specific domain’s messages. This option is enabled by default.
See:


