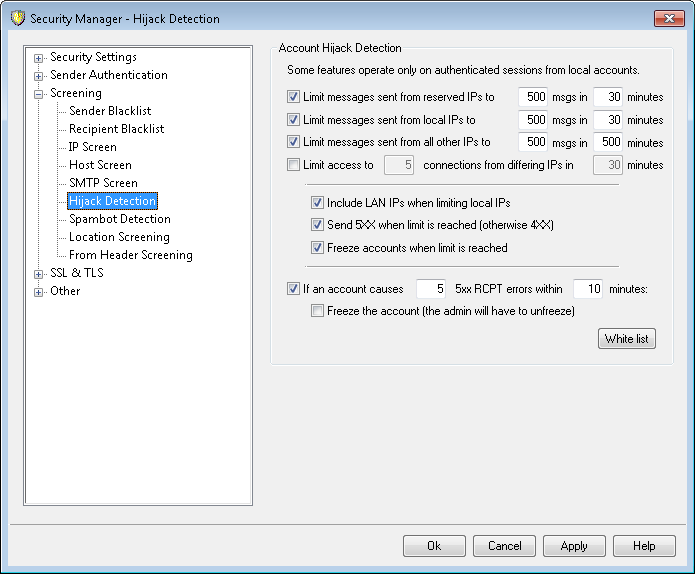
Account Hijack Detection
The options on this screen can be used to detect a possibly hijacked MDaemon account and automatically prevent it from sending messages through your server. For example, if a spammer somehow obtained an account's email address and password then this feature could prevent the spammer from using the account to send bulk junk e-mail through your system. You can designate a maximum number of messages that may be sent by an account in a given number of minutes, based on the IP address from which it is connecting. You can also choose to disable accounts that reach the limit. There is also a White List that can be used to exempt certain addresses from this restriction. Account Hijack Detection is enabled by default.
|
Account Hijack Detection only applies to local accounts over authenticated sessions, and the Postmaster account is automatically exempt. |
Limit messages sent from reserved IPs to [xx] msgs in [xx] minutes
Use this option to prevent MDaemon accounts connecting from reserved IPs from sending more than the specified number of messages in the designated number of minutes. Reserved IP addresses are mostly as defined by RFCs (for example, 127.0.0.*, 192.168.*.*, 10.*.*.*, 172.16.0.0/12, ::1, FD00::/8, FEC0::/10, and FE80::/64).
Limit messages sent from local IPs to [xx] msgs in [xx] minutes
Use this option to prevent MDaemon accounts connecting from any local IPs from sending more than the specified number of messages in the designated number of minutes. Local IPs are all IP addresses configured for any of your MDaemon domain.
Limit messages sent from all other IPs to [xx] msgs in [xx] minutes
Use this option to prevent MDaemon accounts connecting from any other IPs from sending more than the specified number of messages in the designated number of minutes.
Limit access to [xx] connections from differing IPs in [xx] minutes
Use this option to limit the number of connections from different IP addresses allowed within the specified number of minutes. For example, in normal circumstances if your account is accessed from ten different IP addresses within just a few minutes, it is likely the account has been hijacked. This option is disabled by default.
Include LAN IPs when limiting local IPs
By default LAN IPs are included when using the "Limit messages sent from local IPs..." option above. Uncheck this box if you do not wish to include LAN IPs when limiting local IPs.
Send 5XX when limit is reached (otherwise 4XX)
By default when one of the limits is reached, MDaemon will send a 5XX reply code to the hijacked account. Disable this option if you wish to send a 4XX code instead.
Freeze accounts when limit is reached
Check this box if you wish to freeze accounts that attempt to send more than the allowable number of messages. When this happens, the server sends a 552 error, the connection is dropped, and the account is immediately frozen. The frozen account will no longer be able send mail or check its mail, but MDaemon will still accept incoming mail for the account. Finally, when the account is frozen an email is then sent to the postmaster about the account. If the postmaster wishes to re-enable the account, he can simply reply to the message.
If an account causes [xx] 5xx RCPT errors within [xx] minutes
This option monitors how many times an account attempts to send messages to an invalid recipient within a fixed amount of time. One common characteristic of spam email is that the messages are often sent to a large number of invalid recipients, due to the spammer attempting to send them to old email addresses or otherwise guess new ones. Therefore if an MDaemon account begins sending messages to a notable number of invalid recipients in a short amount of time, that is a good indication that the account has been hijacked and is being used to send spam. Using this option with the "Freeze the account..." option below can help stop a hijacked account before too much damage is done. Note: For this option, an invalid recipient is defined as a 5xx error code in response to a RCPT command when trying to send the account's mail.
Freeze the account (the admin will have to unfreeze)
Use this option if you wish to freeze an account when the "If an account causes [xx] 5xx RCPT errors..." threshold above is reached. When this happens the administrator will be notified via email, so that he can investigate the problem and unfreeze the account.
White List
Use the White List to designate any addresses that you wish to exempt from Account Hijack Detection. Wildcards are permitted. For example, "newsletters@example.com" would exempt example.com's "newsletters" MDaemon account, while "*@newsletters.example.com" would exempt all MDaemon accounts belonging to the newsletters.example.com domain. The Postmaster account is automatically exempt from Account Hijack Detection.
