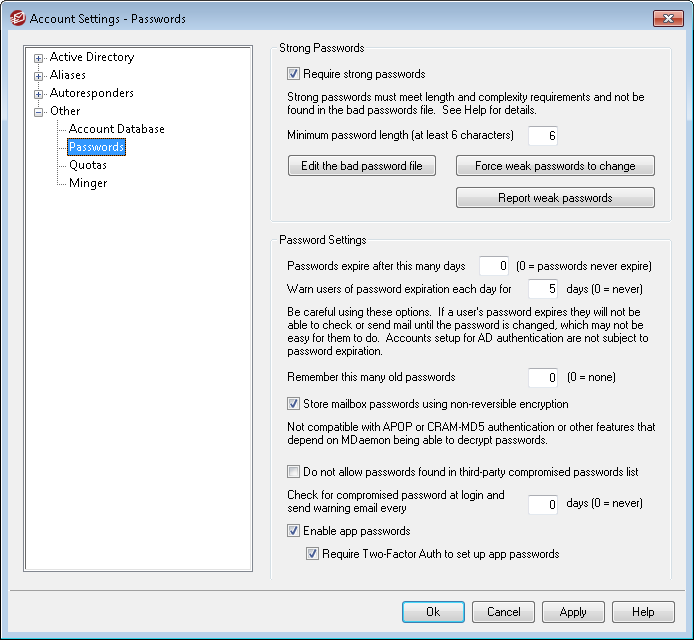
Strong Passwords
Require strong passwords
By default, MDaemon requires strong passwords when creating new accounts or changing existing passwords. Clear this check box if you wish to disable the strong password requirement.
Strong passwords must:
•Meet the minimum length requirement.
•Contain upper and lower case letters.
•Contain letters and numbers.
•Not contain the user's full name or mailbox name.
•Not be found in the bad passwords file.
Minimum password length (at least 6 characters)
Use this option to set the minimum password length required for strong passwords. This must be set to at least 6 characters, but a higher value is recommended. Changing this setting does not automatically trigger a required password change for accounts with passwords shorter than the new minimum, but when those users next change their password this setting will be enforced.
|
Regardless of the minimum setting, passwords can be longer than 15 characters. |
Edit the bad password file
Click this button to edit the bad password file. Entries listed in this file are case insensitive and cannot be used as passwords. If you wish to create more complex or versatile entries, you can use Regular Expressions to do so. Entries beginning with "!" are treated as Regular Expressions.
Force weak passwords to change
Click this button if you wish to force all accounts with a weak password to change their passwords. This will lock out every account with a weak password until the password is changed. The password can be changed by an administrator via the MDaemon interface, or a locked out user can change the password via Webmail or the remote administration interface. When the user attempts to log in using the old password, he or she will be required to create a new one before proceeding.
Report weak passwords
Click this button to generate a report of all MDaemon accounts with a weak password. The report will be emailed to whatever email address you specify after clicking OK.
Password Settings
Passwords expire after this many days (0=passwords never expire)
Use this option if you wish to set a maximum number of days that an account can be accessed before being required to change its password. The default value in this option is "0", which means that passwords never expire. But if you set it to, for example, 30 days then the user will have 30 days to change his or her password, starting from the last time the account's password was changed. Therefore when you initially set an expiration value, any account with a password that hasn't been changed within the specified number of days will immediately have an expired password. When a user's password expires he or she will not be able to access POP, IMAP, SMTP, Webmail, or Remote Administration. The user can, however, still connect to Webmail or Remote Administration where he or she will then be required to change the password before proceeding. Email clients such as Outlook, Thunderbird, and the like cannot be used to change the password. Further, many clients will not even show a helpful error message to users, therefore they may need administrator assistance to figure out why their login is failing.
|
In order for users to be able to change their passwords via Webmail or Remote Administration they must first be granted the "...edit password" web access permission on the Web Services screen. Further, because changing the password may not be easy or possible for some users, you should exercise caution before using this option. |
Warn users of password expiration each day for [xx] days (0 = never)
Accounts with a password that is about to expire can receive a daily reminder email that the password needs to be changed. Use this option to designate the number of days before the password expires that you want MDaemon to start sending these daily emails.
Remember this many old passwords (0=none)
Use this option to specify the number of old passwords that you want MDaemon to remember for each user. When users change their passwords they will not be allowed to reuse old passwords. This option is set to "0" (disabled) by default.
Store mailbox passwords using non-reversible encryption
Check this box if you want MDaemon to store passwords using non-reversible encryption. This protects the passwords from being decrypted by MDaemon, the administrator, or a possible attacker. To do this, MDaemon uses the bcrypt password hashing function, which allows for longer passwords (up to 72 characters), and for passwords to be preserved yet not revealed when exporting and importing accounts. Some features, however, are not compatible with this option, such as weak password detection and APOP & CRAM-MD5 authentication, because they depend on MDaemon being able to decrypt passwords. Non-reversible passwords is enabled by default.
Compromised Passwords
MDaemon can check a user's password against a compromised password list from a third-party service. It is able to do this without transmitting the password to the service, and if a user's password is present on the list it does not mean the account has been hacked. It means that someone somewhere has used the same characters as their password and it has appeared in a data breach. Published passwords may be used by hackers in dictionary attacks, but unique passwords that have never been used anywhere else are more secure. See Pwned Passwords for more information.
Do not allow passwords found in third-party compromised passwords list
Check this box if you do not wish to allow an account's password to be set to one that is found in the compromised password list.
Check for compromised password at login and send warning email up to every [xx] days (0 = never)
With this option you can automatically check each user's password against the compromised passwords list once every specified number of days, when each user logs in. If they are found to be using a compromised password, a warning email is sent to the account and the postmaster. The warning emails can be customized by editing message template files in the \MDaemon\App folder. Since instructions for how a user should change their password may depend on whether the account is using a password stored in MDaemon or using Active Directory authentication, there are two template files: CompromisedPasswordMD.dat and CompromisedPasswordAD.dat. Macros can be used to personalize the message, change the subject, change the recipients, and so on.
App Passwords
App Passwords is an option that can be used to make accounts more secure by creating very strong, randomly generated passwords to be used only in email clients and email apps, since those apps can't be secured by Two-Factor Authentication (2FA). See: App Passwords.
Enable app passwords
All users can create App Passwords for their accounts by default, when signed in to Webmail using Two-Factor Authentication. If you wish to disable App Password support for a specific user, you can do so with the ...edit app passwords option on the user's Web Services page.
Require Two-Factor Auth to set up app passwords
By default, users must be signed in to Webmail using Two-Factor Authentication (2FA) in order to create a new App Password. Disabling this requirement is not recommended. Global Administrators are exempt from this requirement in MDRA, but it is still recommended that they always use 2FA when signing it to MDRA or Webmail.
|
There is an account option on the Account Editor's Settings page that you can use to "Require app password to log in to SMTP, IMAP, ActiveSync, etc." Requiring App Passwords can help protect an account's password from dictionary and brute force attacks via SMTP, IMAP, etc. This is more secure because even if an attack of this sort were to guess an account's actual password, it wouldn't work and the attacker wouldn't know, because MDaemon would only accept a correct App Password. Additionally, if your accounts in MDaemon are using Active Directory authentication and Active Directory locks an account after a number of failed attempts, this option can help prevent accounts from being locked out, because MDaemon will only check the App Passwords, not try to authenticate to Active Directory. |
See:
Account Editor » Account Details
Account Editor » App Passwords

